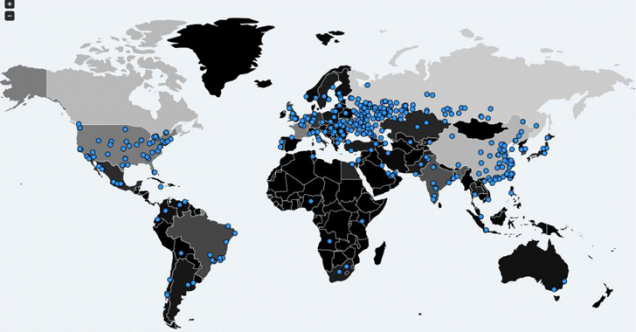
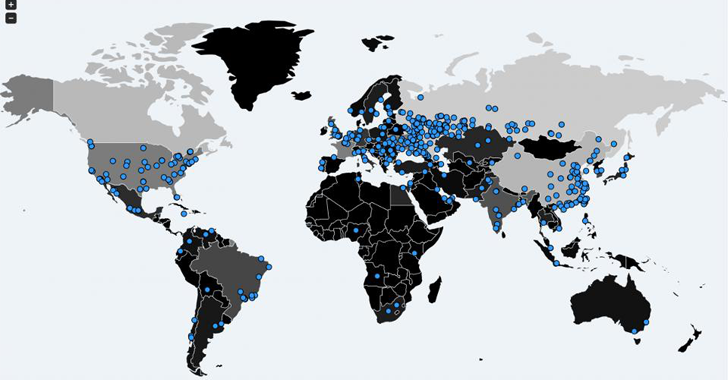
Or also: how does the story of the biggest computer attack ever known to man unfold? While in more than 150 countries around the world are still evaluating the real damages caused by this ransomware, security experts try to understand WannaCry’s origins, scope, and peculiarities. On the one hand, to solve the problems posed by this attack, and on the other to prevent cases like this in the future.
What is WannaCry
Right from the basics: WannaCry is the name given to a ransomware virus that has attacked more than 200,000 computers in over 150 countries around the world last weekend. It exploits a Windows bug that was patched last March, but apparently many computers had not upgraded yet. However, this ransomware can also attack Linux users if Wine – an open source software that allows running Windows programs in Unix environments- is installed.
Who made WannaCry
It is not clear who is behind this attack, although it is certain that ransomware exploits a security flaw in virtually all Microsoft operating systems. This flaw was first found by the NSA, a US government security agency. For years the NSA has used this flaw for its espionage programs, but a few months ago it became public domain when a group of hackers made public this exploit and NSA’s responsibility. On May 14, Microsoft – with a post written by its president and chief legal officer, Brad Smith – issued a rather harsh accusation against the government agency.
And North Korea?
WannaCry looks like the code of softwares used by the Lazarus Group, the North Korean hackers who in 2014 launched the attack against Sony Pictures and last year against a Bangladesh bank. If it’s not evidence per se because similarities might be intentional, left to raise false flags; but similar pieces of code have been removed from the WannaCry versions released in the last few days, which would lead to think that some link is real.
How to defend yourself
As we’ve said more than once, ransomware is particularly insidious because once the attack starts and your data is being encrypted, the key to decrypting them is in the hands of hackers. With a long enough time available, we could decipher our data again, but depending on the type of encryption used it may take years.
The best thing is to be prepared for the disaster because sooner or later something will happen: either a ransomware or the hard disk that breaks down. Combining a regular backup to an updated antivirus and healthy web habits (never open suspect links even if they come from trusted contacts, always wary of zip attachments) can do a lot.