
Dark pattern: how to recognize deceptive techniques of online businesses
We did not have a precise definition of “dark pattern,” but we were aware of the barely-within-the-law techn [...]

Windows 10 S: all you need to know about the new lightweight operating system
Hereafter the launch and the great success of Google Chrome devices, Microsoft realized the need for a lighter and less [...]
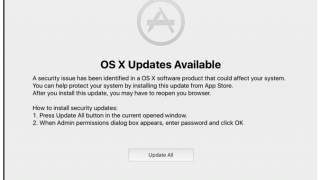
New Mac malware hijacks Internet traffic on compromised servers
Yes, Macs tend to be safer than a Windows PC. Among the various security measures included in the operating system is Ga [...]

Windows 10 Creators Update: Microsoft suggests you not to install the latest update
Microsoft recommends not to manually download and install the latest update to Windows 10 to less experienced users and [...]
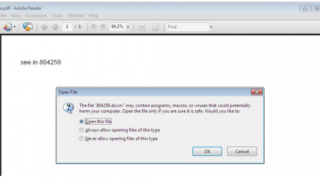
Locky, the new ransomware hidden in the attachment of the attachment
Ransomware is an increasingly widespread and aggressive threat. We are talking about a kind of virus able to block your [...]
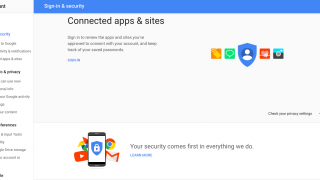
Online account security: how to revoke access to third-party apps
The other day somebody stole the smartphone to a friend on the bus while coming to my house. In addition to the shock an [...]

Smartphone notifications: how to prevent being disturbed
It’s a story we’ve heard many times: we’re too absorbed by our cell phones, we lack attention, we̵ [...]
Microsoft To-Do, the official Wunderlist replacement
In 2015 Microsoft acquired Wunderlist, a great platform for to-do lists with dedicated apps on Windows, Mac, iOS, Androi [...]
