There’s a new threat for Linux devices out there, and it is spreading pretty quickly. Its name is Linux.Proxy.10 and it’s a trojan that turns Linux machines into proxy servers, used during cyberattacks to obfuscate hackers real identities.
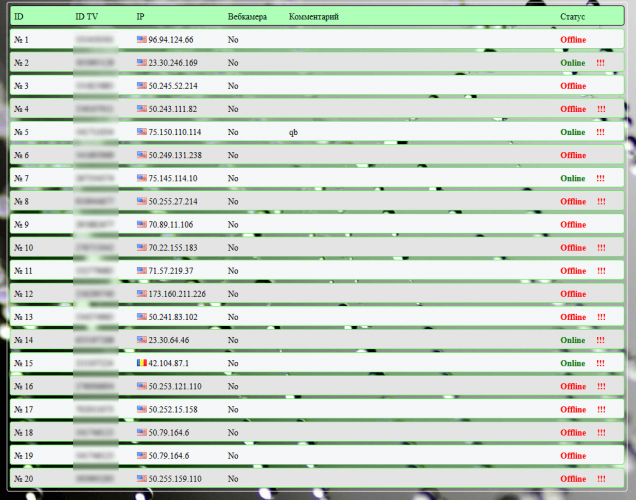
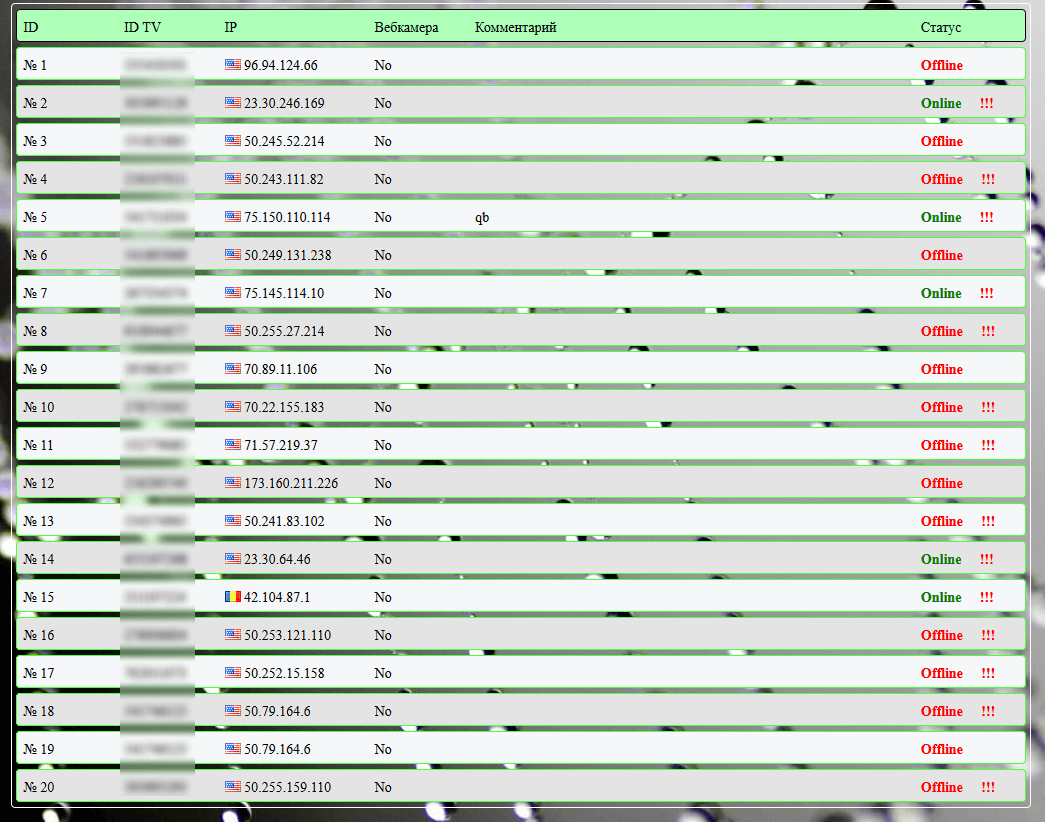
Doctor Web found Linux.Proxy.10 at the end of 2016. Following its evolution, they found that at the beginning of January there was hundreds of infected machines, and the number was growing.
It seems that the trojan is used primarily to get in the system, and create a login for a backdoor account: username “mother”, password “fucker” (yes, just like that). Then it recovers the list of all Linux machines infected, it logs in with each and every one, through SSH. Then it estabilished a proxy server SOCKS5.
This malware uses a simple freeware source code. According to researchers, the same server that host Linux.Proxy.10 has also a software that monitors Spy-Agent computers and a Windows malware, BackDoor.TeamViewer.
How to defend from Linux.Proxy.10
Linux owners can defend from Linux.Proxy.10 limiting or blocking SSH remote access. If you’d like to now if you have been infected, you’d better check regularly if there are new user access.