Different browsers for different needs: a basic list
The browser market is multi-colored, and you can choose different things according to your needs: there is always a larg [...]
There might be a keylogger in your HP devices
Modzero AG’s security experts revealed that some HP device drivers sport a keylogger, which is a malicious code th [...]

Microsoft Build: News from the Developer Conference
Today is the last day of Microsoft Build, their developer conference. It is the annual conference announcing new stuff [...]
Fuchsia, Google’s future operating system
Keeping up with all the difference between Android and Chrome OS is giving you a headache? Don’t worry, Google is [...]

Android malware: 8400 new malicious apps every day
For every new Mac malware discovered we write lots of articles, because of the usual resistance against computer viruses [...]
HandBraker hacked: download server got compromised
HandBrake is one of the most renowned independent Mac software. It allows the conversion of video files to virtually any [...]
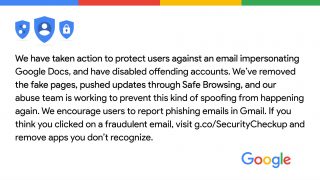
Google Docs phishing: No one is safe, not even Google
Not even Google can be safe from phishing attempts. The other night, many received an email to access a shared document [...]

Dark pattern: how to recognize deceptive techniques of online businesses
We did not have a precise definition of “dark pattern,” but we were aware of the barely-within-the-law techn [...]
