
How to distinguish between good and dangerous free applications
It’s easy to find appealing free applications and services that, however, can hide dangers for your privacy, your [...]

It’s easy to find appealing free applications and services that, however, can hide dangers for your privacy, your [...]
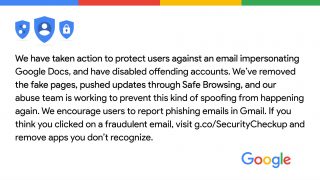
Not even Google can be safe from phishing attempts. The other night, many received an email to access a shared document [...]

We did not have a precise definition of “dark pattern,” but we were aware of the barely-within-the-law techn [...]
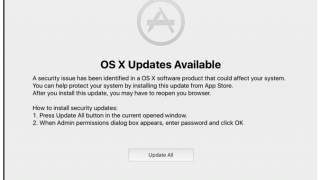
Yes, Macs tend to be safer than a Windows PC. Among the various security measures included in the operating system is Ga [...]

Microsoft recommends not to manually download and install the latest update to Windows 10 to less experienced users and [...]
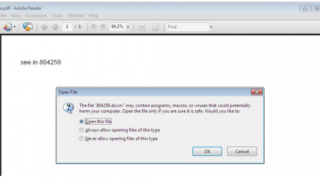
Ransomware is an increasingly widespread and aggressive threat. We are talking about a kind of virus able to block your [...]
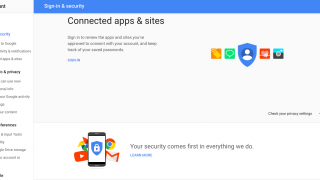
The other day somebody stole the smartphone to a friend on the bus while coming to my house. In addition to the shock an [...]

If you have an iPhone and you have updated to iOS 10.3.1 you’re safe. Every Android user has to be careful, thou. Proj [...]