Researchers found a huge hole in one of the most popular WordPress plugins: a bug that threatens 1 million websites created on the popular CMS platform. The sites at issue are vulnerable to hacks that allow visitors to access passwords and private info directly from the database (of course, certain conditions must be met for this to happen).
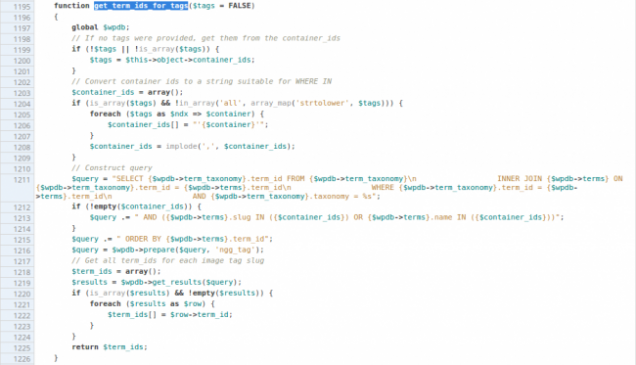
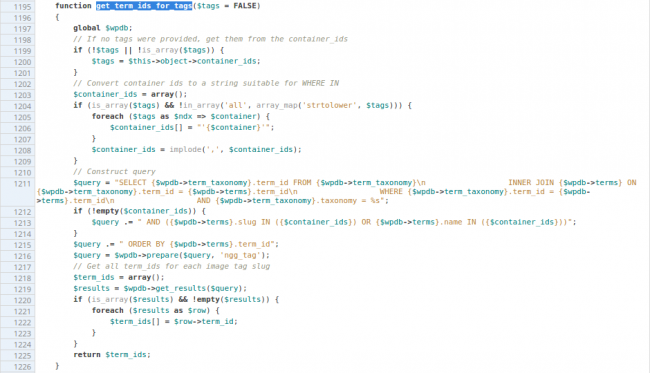
The vulnerability stems from a bug that allows a SQL code injection through plugin NextGEN Gallery, installed on more than 1 million sites. Before being fixed with an update, this bug allowed visitors to enter a third-party code on the site during a SQL call. Hackers could exploit this condition to quickly send commands to the database that powers a standard WordPress backend. Changing the URL of a gallery of images created with the plugin NextGEN Basic TagCloud was enough.
The most vulnerable are those sites that have not updated the plugin to the latest version and allow users registration and posts creation. Hackers can, in fact, create an account, write a post and use the shortcode suited to exploit the flaw in NextGEN Gallery.
This is a critical flaw, with 9 out of 10 rating on the DREAD scale used by researchers at Sucuri. The version affected by the bug is NextGEN Gallery 1.2.79. To avoid any danger upgrade as soon as possible.